New address bar spoofing vulnerabilities found in DuckDuckGo and Tap Browser, disclosed by Cyber Citadel researchers, could affect millions of iOS and Android users
Cyber Citadel’s Lead Security Researcher Rafay Baloch and Security Researcher Muhammad Samak disclosed address bar spoofing vulnerabilities today in the DuckDuckGo browser for iOS, Video Downloader Browser for Android and Tap Browser for iOS mobile web browser applications
These flaws can be exploited, by potentially tricking users into supplying sensitive information to a malicious website. Our discovery found that a malicious attacker could easily lead the unsuspecting users to believe that they are visiting a legitimate website as the address bar points to the correct website. It is pertinent to mention here that, Cyber Citadel, as a part of its responsible disclosure policy gave a time frame of 60 days to all three browsers to fix these vulnerabilities. At the time of publishing this disclosure, the issue was only addressed by DuckDuckGo.
Address Bar Spoofing Vulnerabilities
Mobile web browser address bar spoofing allows an attacker to change the URL of a malicious website to one that represents a legitimate website, i.e. google.com, bing.com, facebook.com, or apple.com, for example.
This vulnerability bypasses the security certificates built into most modern mobile address bars. Desktop web browsers designate a website as safe by the lock icon on the far left of an address bar that ‘guarantees’ a website has a valid SSL certificate and is, therefore, secure.
On the other hand, security indicators on mobile devices are harder to find, due to the lack of screen real-estate, and restrict the ability to interrogate security elements. With typical users being unaware of website validation on mobile web browsers, cybercriminals are free to insert fake malicious pages with spoofed URL addresses.
Address bar spoofing traditionally scores approximately 4.3 out of 10 on the Common Vulnerability Scoring System (CVSS), technically assigning address bar spoofing with a moderate impact.
However, given the substantial 667% rise in spear-phishing attacks experienced during the COVID-19 pandemic, mobile address bar spoofing should arguably be held in higher regard. In a survey conducted by Mimecast, 2.1 million domains were tied to phishing attacks, with 47% of successful attacks making use of fraudulent websites. The disclosed DuckDuckGo and Tap Browser vulnerabilities directly tie into these figures by allowing cybercriminals to make fraudulent websites more believable and, therefore, more successful in harvesting sensitive information.
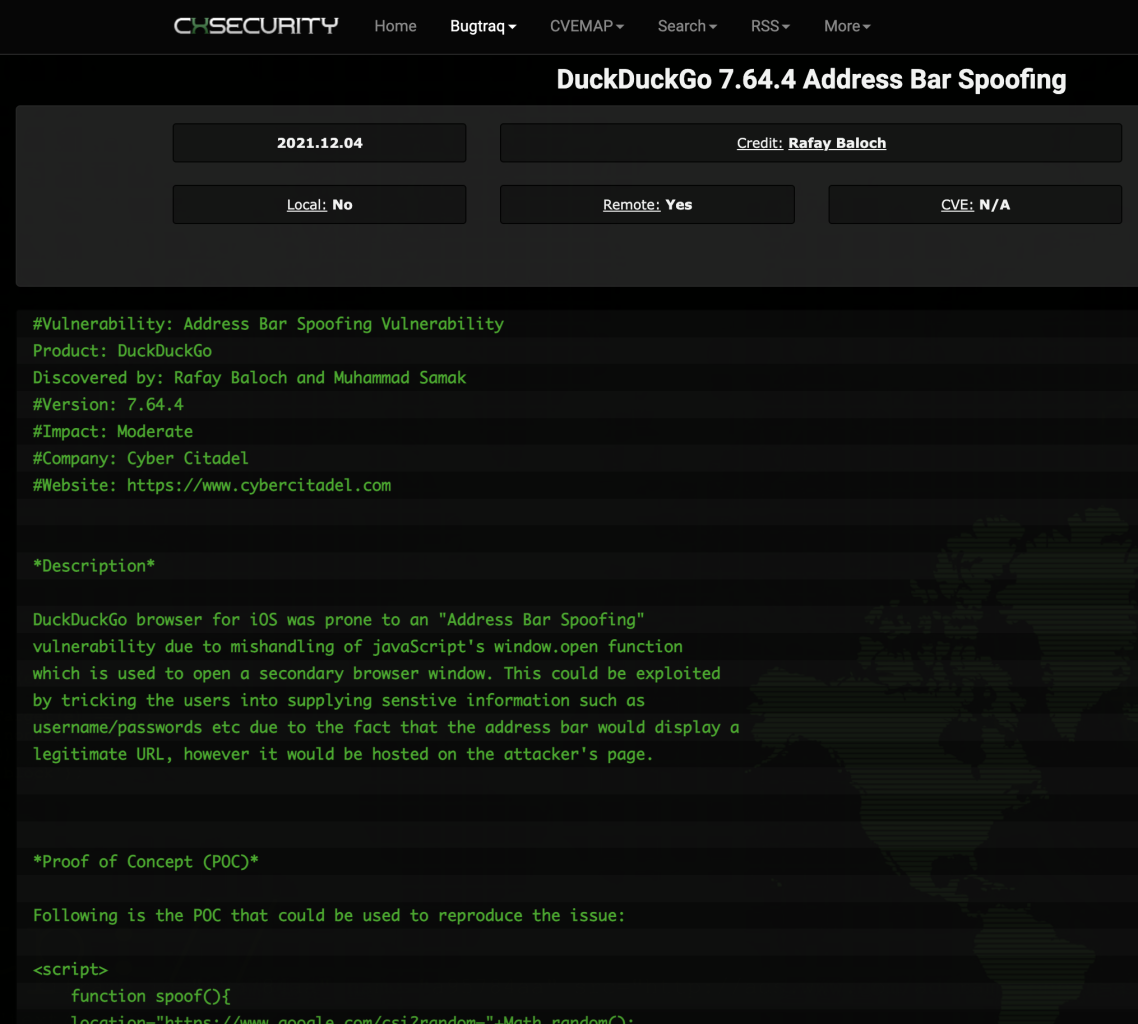
DuckDuckGo
‘Hatched’ in 2008, DuckDuckGo has become a popular web browsing tool downloaded 5 million times per month as a mobile application or desktop extension. It gives users the ability to browse the web privately, while protecting users from internet trackers.
The recent address bar spoofing CVE-2021-44683 disclosed by Baloch and Samak considerably weakens DuckDuckGo’s promised privacy protections for iOS users.
In the proof of concept (POC), Baloch and Samak revealed that version 7.64.4 of DuckDuckGo’s iOS application was prone to address bar spoofing due to a mishandling of JavaScript’s window.open function used to open a secondary window.
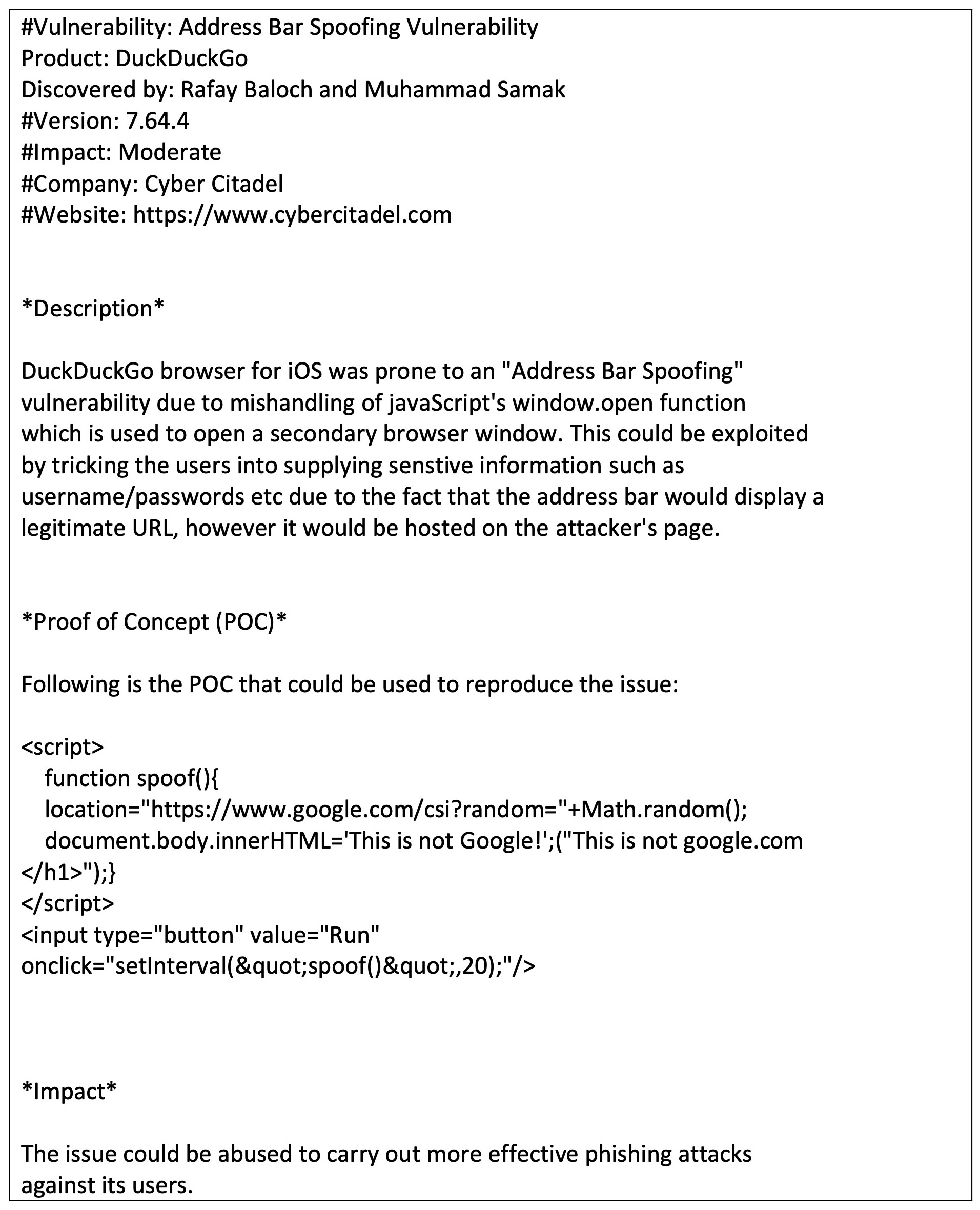

When exploited by a bad actor, an address bar in a secondary window opened in DuckDuckGo would display a legitimate URL despite being hosted by an attacker. This fraudulent page could be designed to trick users into supplying sensitive PII such as usernames and passwords.
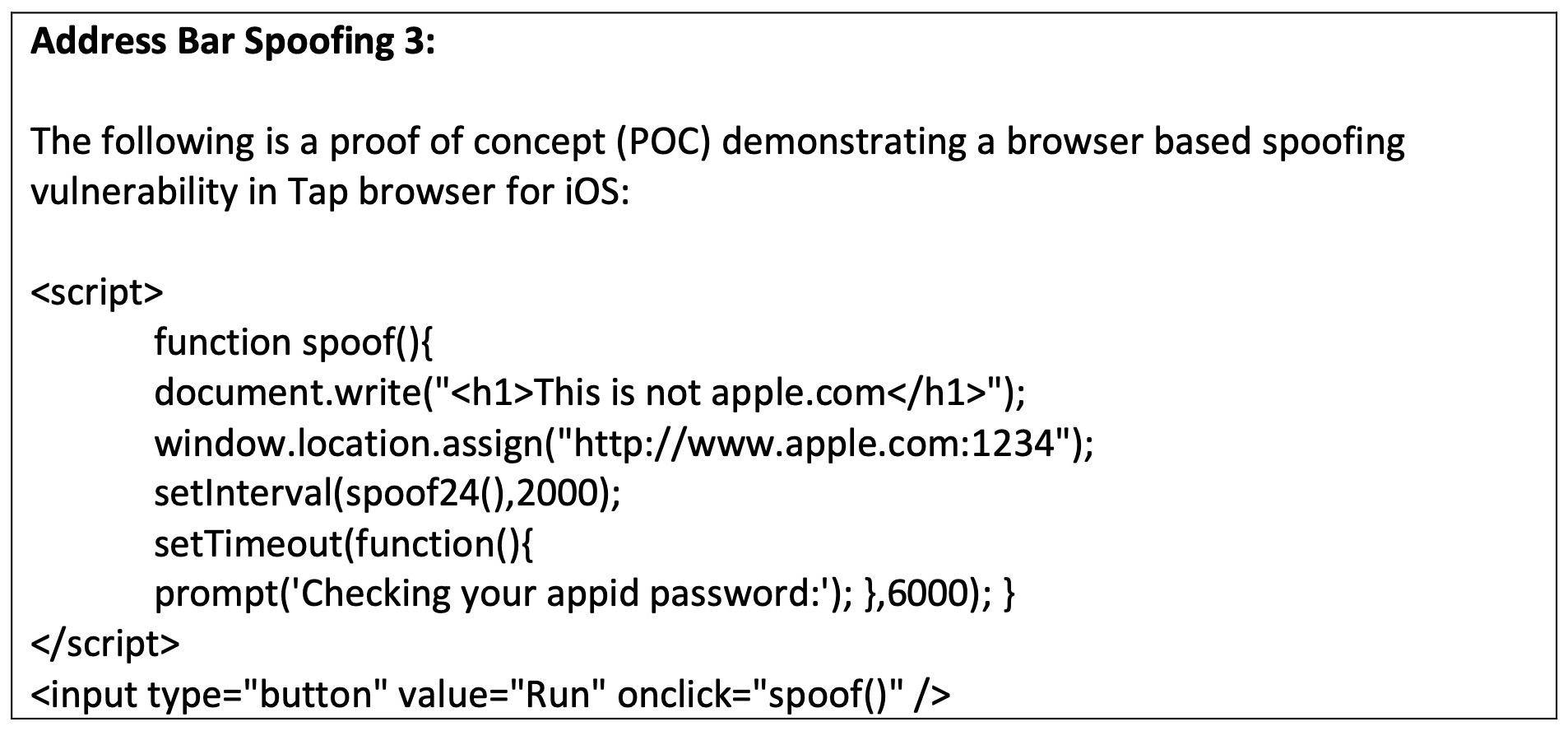
Tap Browser
Built exclusively for iOS, Tap Browser is used for its additional web browsing functionalities such as easy navigation icons, in-app media players and an in-built VPN service.
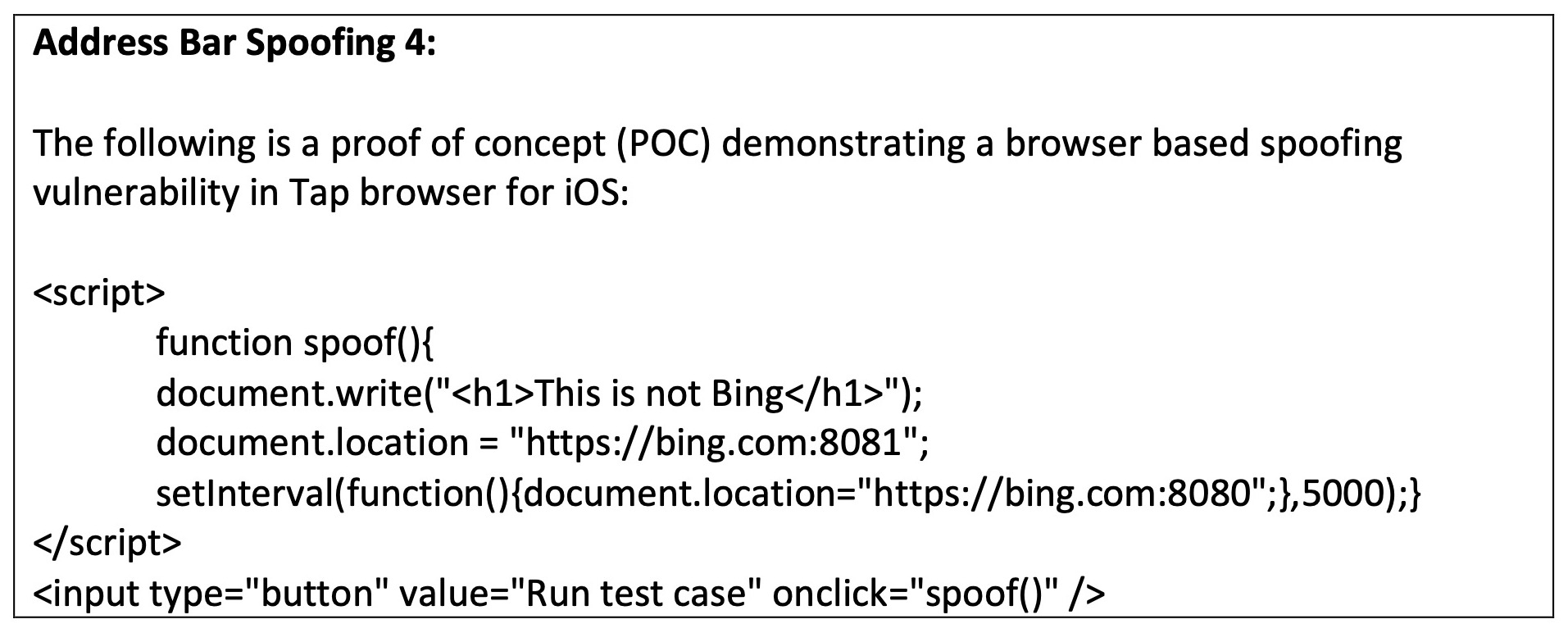
Although a relatively low user base (7,000 downloads), the Tap Browser address bar spoofing vulnerability part of the CVE-2021-44683 disclosed by Baloch and Samak was open to secondary window exploitation.
In the POC, Baloch and Samak demonstrated how a secondary window could be spoofed by a bad actor to replicate Facebook, Gmail, Apple and Bing browsers.






Response from Vendors
| Vendor | Service | Version | Platform | Reported Date | Fixed | CVE |
| DuckDuckGo | DuckDuckGo | 7.64.4 | iOS | 26/09/21 | 7.64.18 | CVE-2021-44683 |
| Tap Browser | Tap Browser | 1.2 | iOS | 26/09/21 | Unfixed | N/A |
HexCon Talk on Address Bar Spoofing Flaws
This is not the first time, Rafay Baloch has found flaws in browsers. In October 2021 at the Hexcon Security conference, Rafay Baloch presented his findings across various mobile browsers titled “What you see, is not always what you get”. Various categories of address bar spoofing vulnerabilities were discussed along with how these vulnerabilities can be used to abuse security mechanisms in browsers.
Previous CVEs Disclosed by Cyber Citadel Researchers
This disclosure by Cyber Citadel security researchers comes a year after Rafay Baloch teamed up with Rapid7’s Director of Research Tod Beardsley to disclose a similar address bar vulnerability across seven mobile web browsers including Apple Safari and Opera Touch.
Baloch reported multiple vulnerabilities on Chrome and Firefox browsers in 2016, Google Inc’s Android browser in 2014, and was paid a total of US$10,000 for reporting a Code Execution/Command Execution vulnerability on PayPal’s sub-domain in 2012. He is considered one of the world’s top ethical hackers and listed in the Google, Facebook, PayPal and Microsoft Hall of Fame.